Setup
iSchool IT can set up NetID authentication for UW AWS accounts. The process requires an AWS account number, so new AWS accounts will have to be created first:
- Once the AWS account # is created, iSchool IT sends a request for UW-IT to create a ‘stem’ in the UW groups service.
- iSchool IT uses the AWS group stem to create one or more ‘role-based’ groups and corresponding roles (with matching names) in AWS IAM.
- iSchool IT always creates an ‘admin’ role group that contains the project admins and iSchool IT, and allows these members to have full rights on the AWS account. This group also doubles as an email list for AWS communications.
- Project ‘owners’ (e.g. faculty associated with the AWS account) are also added as ‘member managers’ of the UW groups. This allows the project owners to directly add/remove members from the access role groups for the AWS account.
- Other roles that only grant selective access (e.g. ”ProjectA-viewer”) can also be created based on specifications from the AWS project admins.
If you need to make create/remove roles after the initial setup, or transfer ownership of an AWS account, please send an email to ihelp@uw.edu
Usage
Login
Once the UW groups are set up, users should use this AWS NetID login link:https://idp.u.washington.edu/idp/profile/SAML2/Unsolicited/SSO?providerId=urn:amazon:webservices
- If a user is a member of more than one AWS groups in the UW groups service, then the UW authentication server will display a menu of the available AWS accounts/roles that the user can login to.
Adding / Removing Users
AWS project owners can add/remove users from the UW groups that represent the access roles for their AWS account(s).
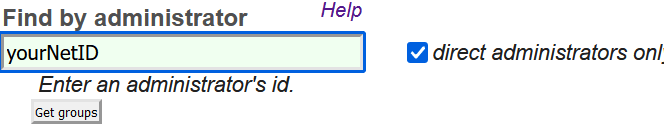
To find AWS groups associated with your NetID, login to your UW groups listing and use your browser’s search function (CTRL+F in Chrome) to find the phrase “u_weblogin_aws”… You can also use the UW groups search function and type your own netid into the “Find Administrators” section:

Any AWS role-based access groups in the results will be listed in the following format of “u_weblogin_aws_AWSACCT###_AWSAccountName-RoleName“. Example:
- u_weblogin_aws_1234567890_awsawsomeproject-admins
To verify who can modify the membership, click on the link below the group name and look near the bottom of the “General Information” page for “Member managers.”
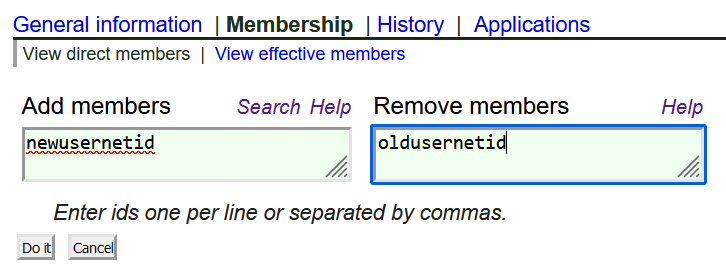
Anyone list in the “Member managers” section may add/remove users by selecting the ‘membership’ link near the top and entering one or more NetIDs in the Add or Remove boxes: